Using AI to Conclusively Address Growing Threats
The goal of cybersecurity is to reduce the risks and protect IT assets from malicious attackers. Many organizations still opt for 'good enough' cybersecurity practices due to budget constraints and this leads to a constant wave of security incidents.
When Good Enough Isn’t Enough
Many companies invest in traditional signature-based protection cybersecurity products but are still getting hacked. Hackers are becoming more sophisticated; they know how to leverage on Artificial Intelligence and Machine Learning to the fullest to mount ever more sophisticated attacks!

Detection of Advance Threats
Detecting Insider Threats
Slow Response Time to Detect Threats
Security Threats Missed
Avg. Days Attackers Discovered Within Network

Advanced Threats and Incapability of Current Solutions
Cyber Security Measures Are Just Too Complex
It is proven that using Security Incident and Event Management (SIEM) can be too complicated to integrate. SIEM requires massive collection of data – aggregating and normalizing them – and this procedure involves a number of other correlating disparate technologies. As a result, SIEM deployments could take months to complete.
Hackers Are Already Well-Equipped with AI Technology
Hackers nowadays are becoming more aggressive with their attacks. The irony is: they are using Artificial Intelligence and Machine Learning to learn the target’s IT network environment. As a result, hackers are more capable and proficient at what they are doing than ever before. They are also harder to detect.

Cybots Revolutionizes Security Approach
MDR (short for Managed Detection Remediation), distributed by Cybots, is a software developed by CyCraft, a prestigious Artificial Intelligence and Machine Learning based Cybersecurity company that employs advanced detection engines of cyber threats that allow businesses to stay ahead of the attackers. Cybots powers Security Operations Centres (SOCs) using a wide range of proprietary and award-winning tools – from AI Driven Managed Detection and Response (MDR) to SOC Operations software and Threat Intelligence, and from Health Checks and Automated Forensics to Incident Response services. Cybots MDR has been employed to secure government agencies, Fortune Global 500 firms, top banks and financial institutions, critical infrastructure, airlines, telecommunications, and hi-tech firms, globally. With CyCraft, security breaches do not even begin.
Get Cyber Health CheckWhy Cybots
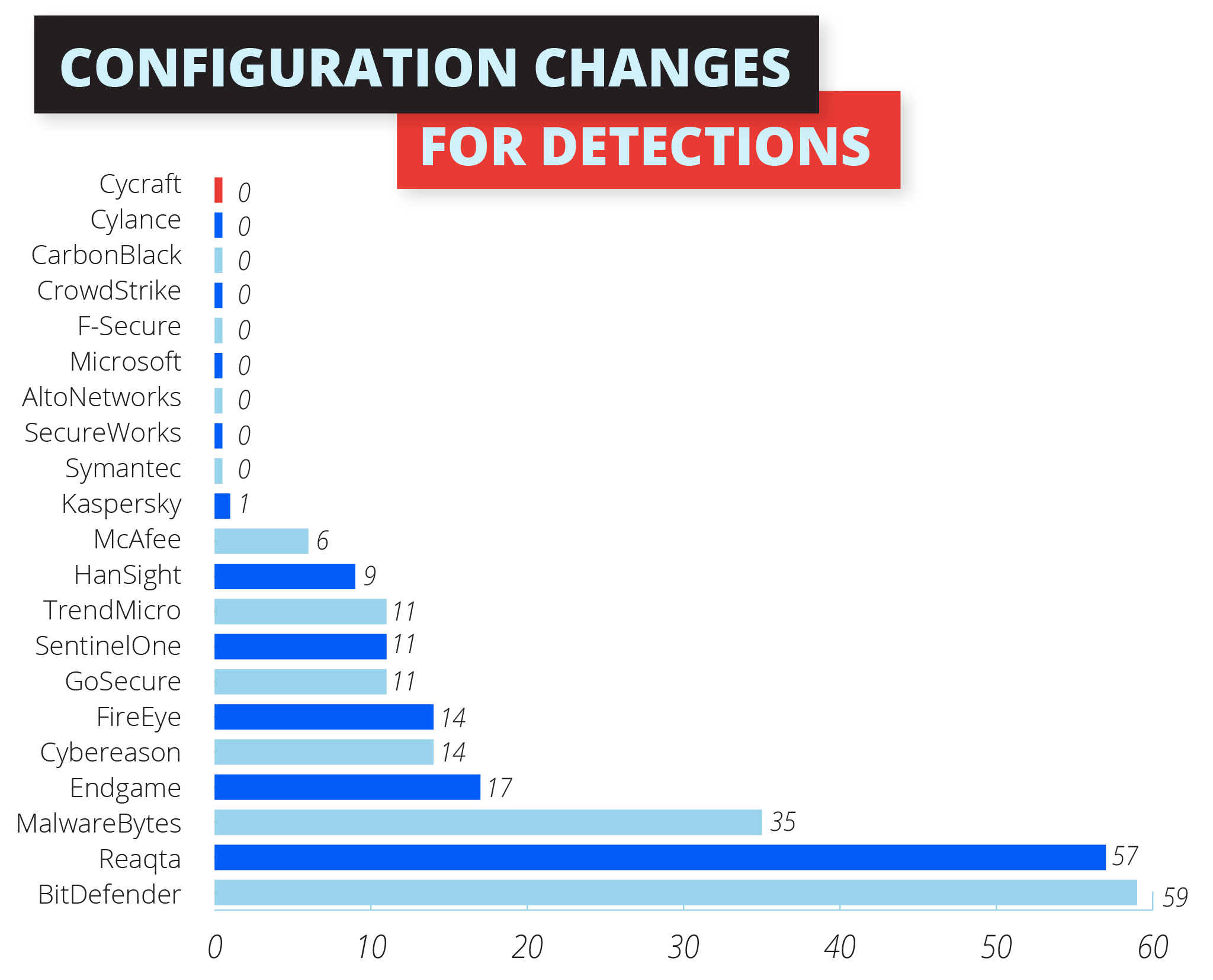
As the only Asian company out of 21 companies invited, CyCraft emerged as the leader recording the highest number of alert detections involving Advanced Persistent Threat 29 (APT 29) during the latest round of MITRE ATT&CK® Evaluations, recording zero configuration changes. This result validates CyCraft’s world-leadership in terms of thoroughness, accuracy, and results-oriented focus with regards to cybersecurity.

Awards & Recognition
Gold Winner Cyber Security Company in Asia
Gold Winner Cyber Security Product - APT Protection
Gold Winner Artificial Intelligence Security
Gold Winner Bot Defense
Gold Winner Breach Protection in Asia
Gold Winner Change Detection
Gold Winner Critical Infrastructure Security
Gold Winner Cyber Threat Intelligence
Gold Winner Detection and Response Solution
Gold Winner Endpoint Security
Gold Winner in Forensics
Gold Winner in Incident Response
Gold Winner in Insider Threat Solution
Gold Winner in User and Entity Behaviour Analytics (EUBA)
Gold Winner in Machine Learning
Gold Winner in Managed Detection and Response
Gold Winner in Managed Security Services
Gold Winner in Security Analytics
Gold Winner in Security Automation
Gold Winner in Security Investigation
Gold Winner in Security Managment
Gold Winner in Secuirty Monitoring
Gold Winner in Security Orchestration, Automation and Response
Gold Winner in Threat Detection, Intelligence and Response
Gold Winner in Threat Hunting
Significant Results in MITRE ATT&CK ® Evaluations
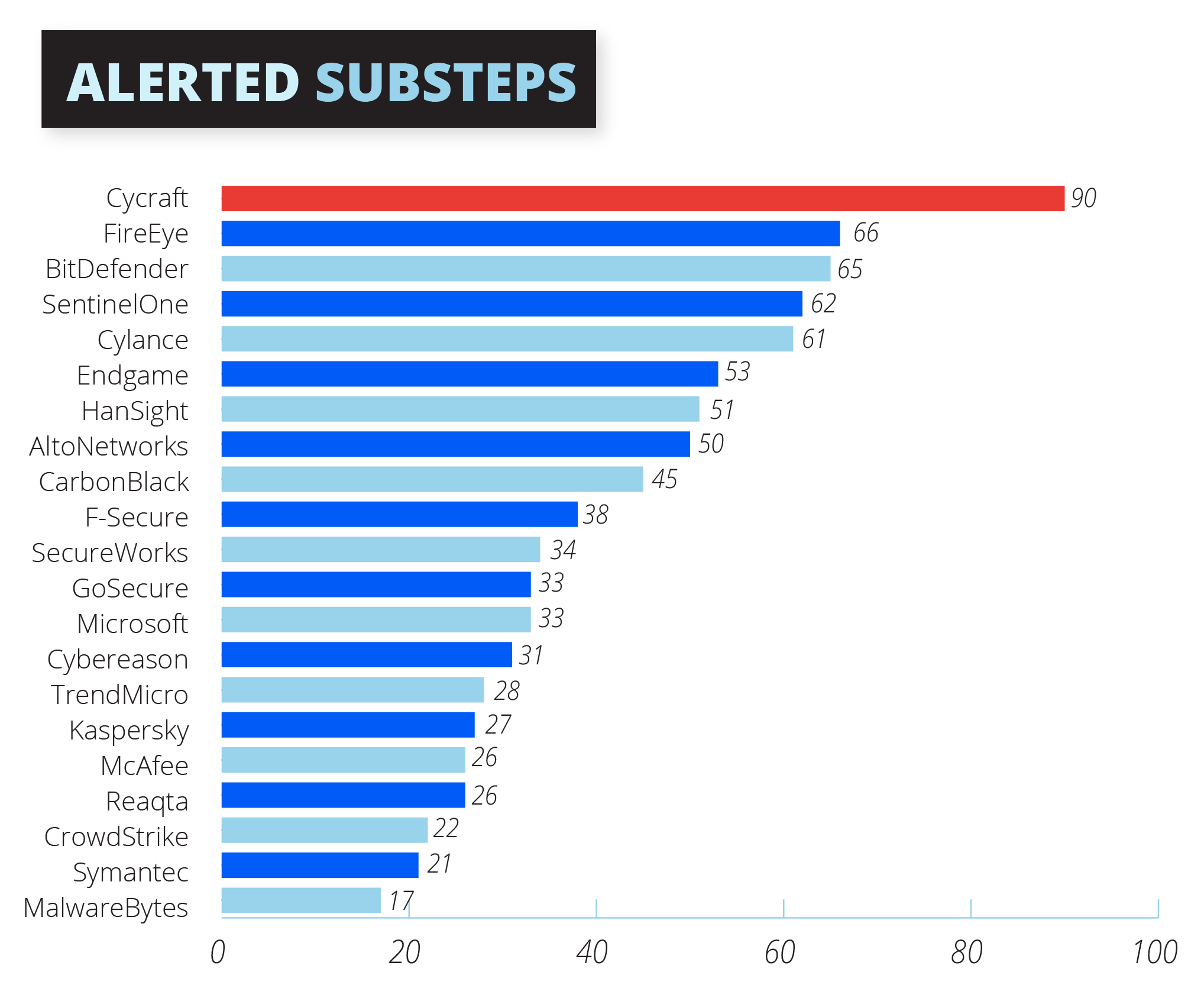
Number One in Alerting
CyCraft’s AI is Number One in generating the most comprehensive, accurate yet simple alerts against the Advanced Persistent Threat 29 (APT29) challenge. This involves 90 sub-steps in the evaluation, which include the General, Tactic, and Technique detections as per MITRE distinction.
Rather than just passively detecting adversarial behaviours, the alerts allow a vendor to immediately prioritize that behaviour and communicate it to the SOC Operations team so they will be able to arrest the problem immediately.
Zero Configuration Changes
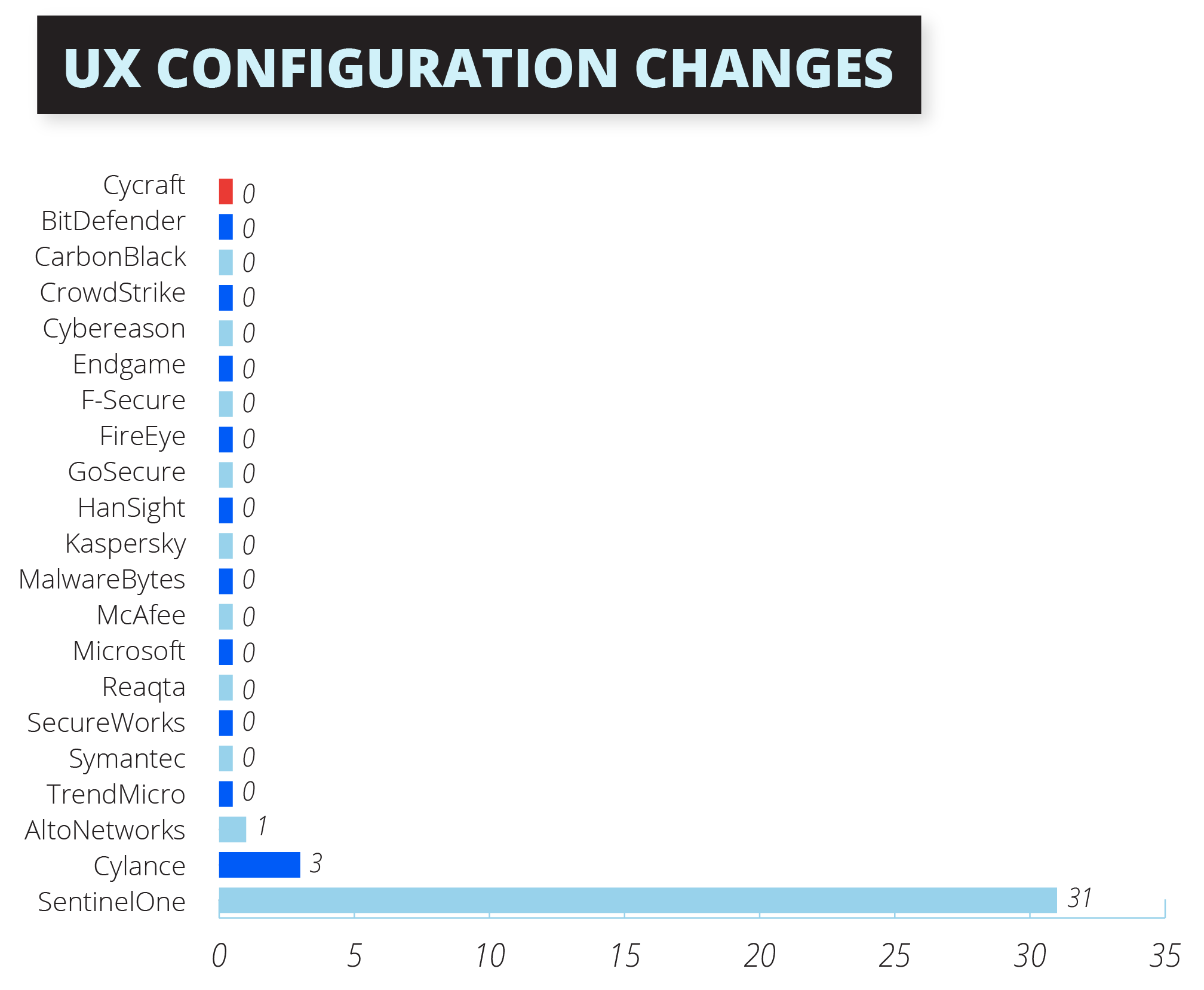
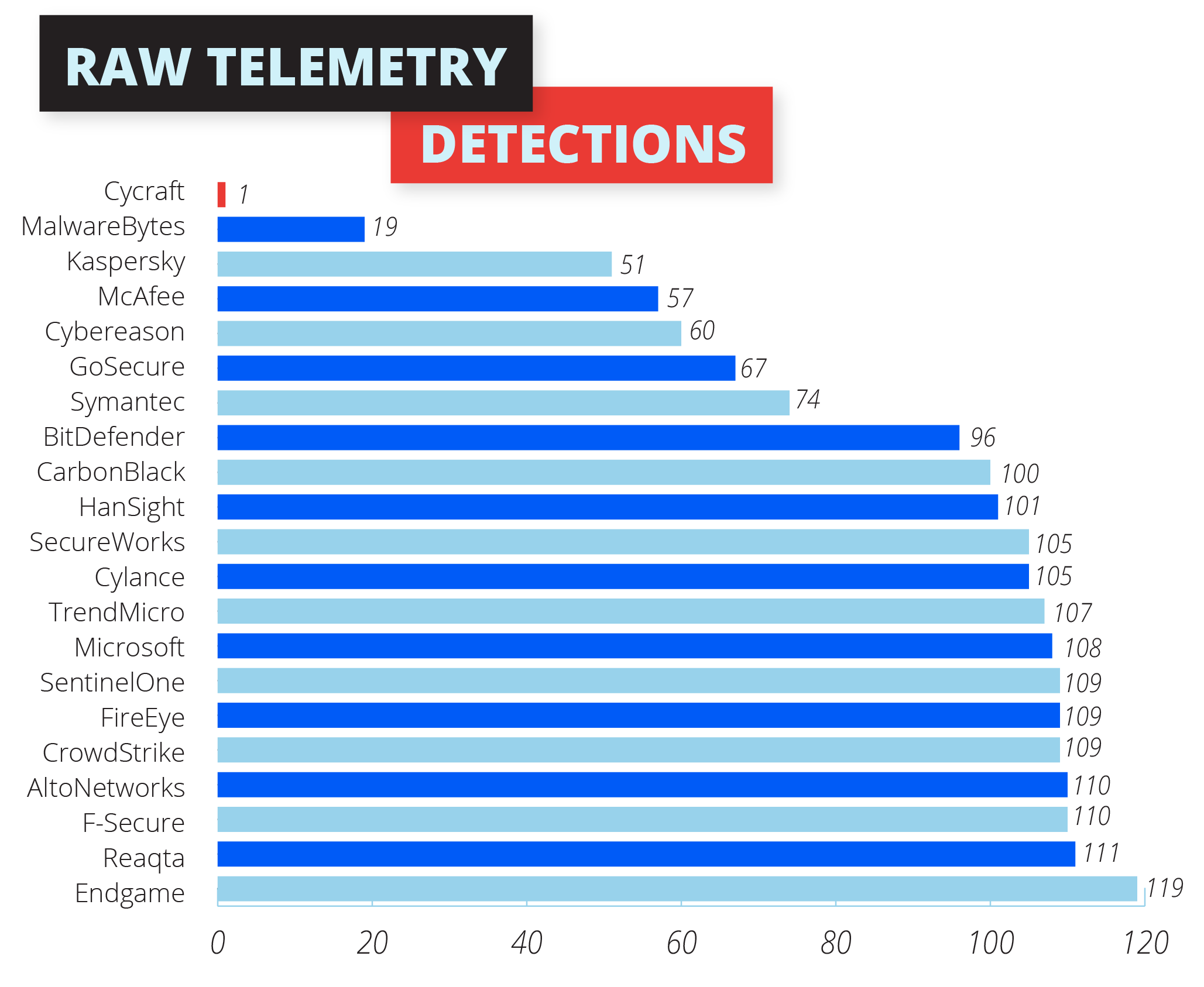
Telemetry: The New Perspective
Further, CyCraft is able to generate a comprehensive storyline and assess cyberattacks across all systems, enabling security practitioners to effectively tackle the ATT&CK-emulated adversary.
Due to the superiority of AI on CyCraft’s sensor and its CyCraft AIR cloud platform, CyCraft is able to manage outcomes more meaningfully. Instead of the typical low-value telemetry detections, CyCraft registers the detections at higher levels on the MITRE classification: General, Tactic, and Technique.
What differentiates the proprietary AI engine is CyCraft AIR’s ability to carry out auto investigation using the raw telemetry data. This is a unique differentiating capability.
The Solution
Cybots is the Next Generation Security Operations Centre (SOC) that is powered by Artificial Intelligence and Machine Learning. As a result, the Tier 1 operations will be controlled by a machine rather than a human. Cybots MDR can therefore provide round-the-clock tracking for security threats to your network. This gives you the peace of mind that all your devices will stay protected at all times.
CyBots does all these in a Flash
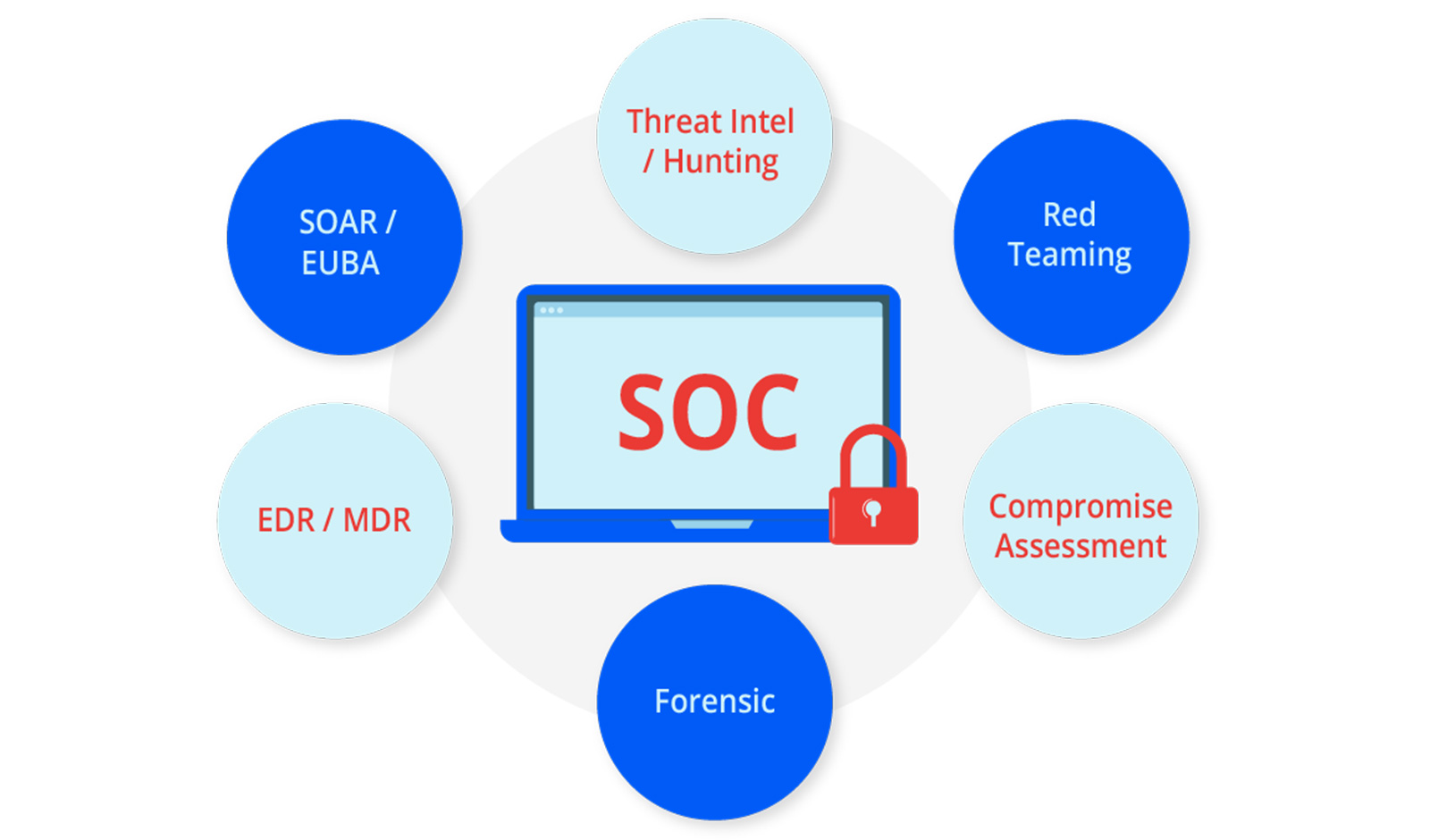
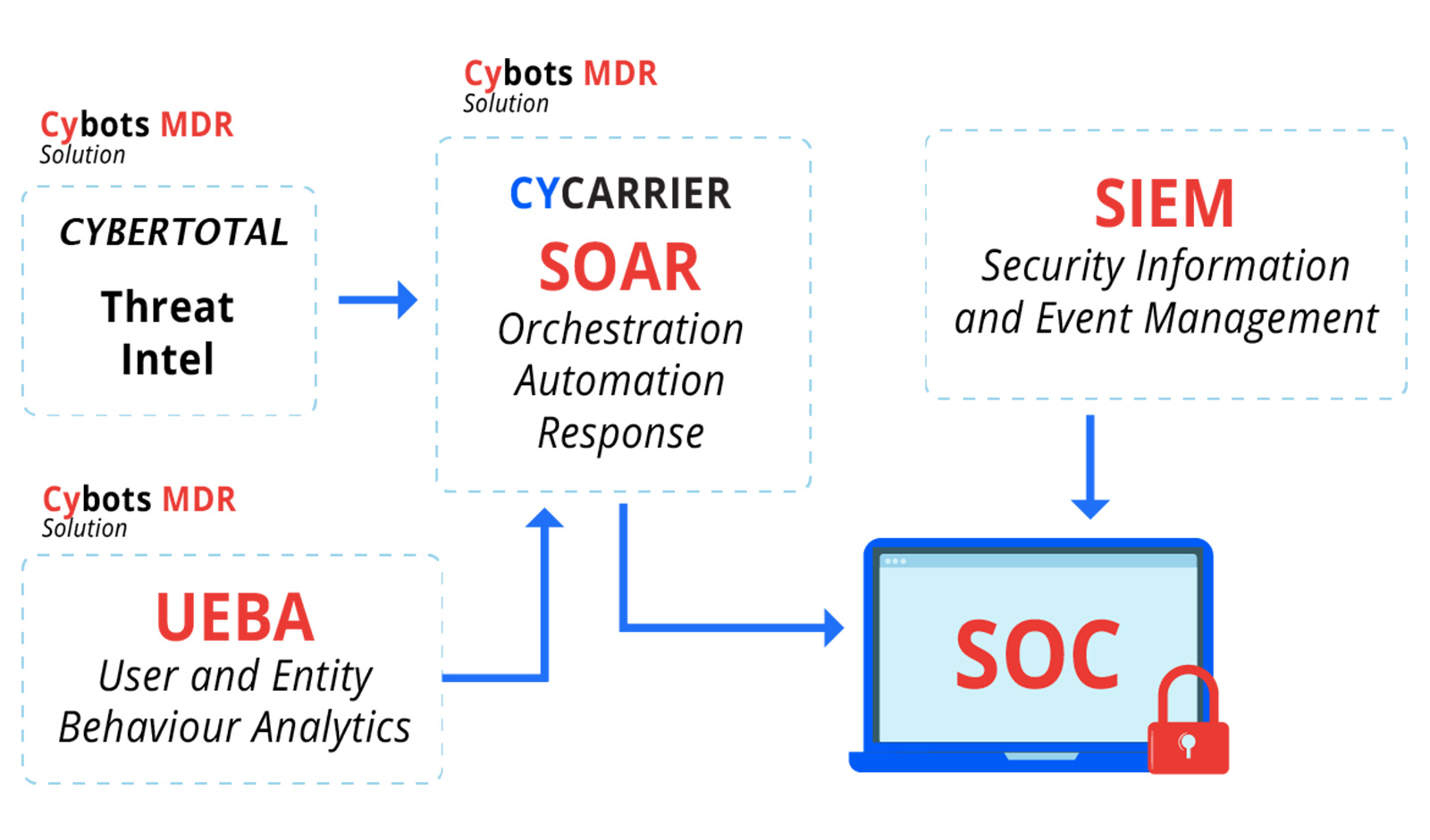
Cybots is a fully AI-Automated Detection application that is fully automated using Xensors, SOAR and Cyber Threat Intelligence (Cybertotal). This provides Remediation Solutions that will offer a guaranteed assurance when it comes to protection of your devices.
dbix is the authorized reseller for CyBots from CyCraft
The Solution Architecture
Continuous Threat Hunting
AI-powered & forensic-based threat hunting inspects thousands of endpoints simultaneously to reduce dwell time and eliminate hidden threats residing on your endpoints.
Situation Awareness
Identifying indicators of compromise and suspicious behaviors to assess the state of your cyber posture and determine if a breach happened or is actively occurring.
Root Cause Analysis
Utilize AIR to demystify root cause and present storyline of breach to understand how and where it occurred and harden your cyber resilience.
Automated Alert Validation
Cybots understands your security teams review several thousand alerts each day, on average. The developed CyberTotal analyzes intelligence that matters to your security team and automatically prioritizes for you.
Auto Incident Response
Cybots, powered by CyCarrier technology, combines Forensic Telemetry Analysis (FTA), lateral movement correlation, malware modeling and global threat intelligence to one CyCarrier platform for orchestrated and automated modern security operation.
AN OUNCE OF PREVENTION IS WORTH A POUND OF CURE.
CyBots protects more than just a company. It protects the interests of all stakeholders – the investors, the operations team, the IT team, and more importantly, you as the customer. Prevention is better than cure.
Check Your Cyber Health Now.
About MITRE
MITRE’s mission-driven teams are dedicated to solving problems for a safer world. Through our collaboration with federal-funded R&D centres, we work closely with the government and the industry to address cyber security threats to safeguard our nation from cyber security threats.
www.mitre.org
About ATT&CK
ATT&CK® was created under MITRE’s internal research program based entirely on published, open-source threat information. Increasingly, ATT&CK is driven by valuable contributions from external sources. Cybersecurity vendors may apply to participate in the next round of the ATT&CK Evaluations, which will feature the Carbanak and FIN7 threat groups as the emulated adversaries.
About APT29
The adversary, APT29 is a group that cybersecurity analysts believe operates on behalf of the Russian government; they have, since 2015, breached the security measures established by the Democratic National Committee. MITRE used its ATT&CK knowledge base to examine the ability to detect the tactics and techniques used by APT29 when emulating the group.
